- What is Computer Security?
- Computer Security Threats
- Why is computer security important?
- Best computer security practices.
What is computer security?
Computer security basically is the protection of computer systems and information from harm, theft, and unauthorized use. It is the process of preventing and detecting unauthorized use of your computer system.
There are various types of computer security which is widely used to protect the valuable information of an organization.
What is Computer Security and its types?
One way to ascertain the similarities and differences among Computer Security is by asking what is being secured. For example,
- Information security is securing information from unauthorized access, modification & deletion
- Application Security is securing an application by building security features to prevent from Cyber Threats such as SQL injection, DoS attacks, data breaches and etc.
- Computer Security means securing a standalone machine by keeping it updated and patched
- Network Security is by securing both the software and hardware technologies
- Cybersecurity is defined as protecting computer systems, which communicate over the computer networks
It’s important to understand the distinction between these words, though there isn’t necessarily a clear consensus on the meanings and the degree to which they overlap or are interchangeable.
So, Computer security can be defined as controls that are put in place to provide confidentiality, integrity, and availability for all components of computer systems. Let’s elaborate the definition.
Components of computer system
The components of a computer system that needs to be protected are:
- Hardware, the physical part of the computer, like the system memory and disk drive
- Firmware, permanent software that is etched into a hardware device’s nonvolatile memory and is mostly invisible to the user
- Software, the programming that offers services, like operating system, word processor, internet browser to the user
The CIA Triad
Computer security is mainly concerned with three main areas:
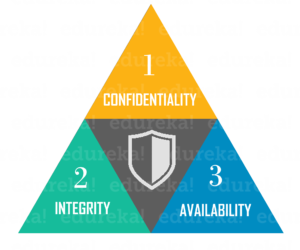
- Confidentiality is ensuring that information is available only to the intended audience
- Integrity is protecting information from being modified by unauthorized parties
- Availability is protecting information from being modified by unauthorized parties
In simple language, computer security is making sure information and computer components are usable but still protected from people or software that shouldn’t access it or modify it.
Now moving forward with this ‘What is Computer Security?” article let’s look at the most common security threats.
Computer security threats
Computer security threats are possible dangers that can possibly hamper the normal functioning of your computer. In the present age, cyber threats are constantly increasing as the world is going digital. The most harmful types of computer security are:
Viruses
 A computer virus is a malicious program which is loaded into the user’s computer without user’s knowledge. It replicates itself and infects the files and programs on the user’s PC. The ultimate goal of a virus is to ensure that the victim’s computer will never be able to operate properly or even at all.
A computer virus is a malicious program which is loaded into the user’s computer without user’s knowledge. It replicates itself and infects the files and programs on the user’s PC. The ultimate goal of a virus is to ensure that the victim’s computer will never be able to operate properly or even at all.
Computer Worm
 A computer worm is a software program that can copy itself from one computer to another, without human interaction. The potential risk here is that it will use up your computer hard disk space because a worm can replicate in greate volume and with great speed.
A computer worm is a software program that can copy itself from one computer to another, without human interaction. The potential risk here is that it will use up your computer hard disk space because a worm can replicate in greate volume and with great speed.
Phishing

Disguising as a trustworthy person or business, phishers attempt to steal sensitive financial or personal information through fraudulent email or instant messages. Phishing in unfortunately very easy to execute. You are deluded into thinking it’s the legitimate mail and you may enter your personal information.
Botnet
 A botnet is a group of computers connected to the internet, that have been compromised by a hacker using a computer virus. An individual computer is called ‘zombie computer’. The result of this threat is the victim’s computer, which is the bot will be used for malicious activities and for a larger scale attack like DDoS.
A botnet is a group of computers connected to the internet, that have been compromised by a hacker using a computer virus. An individual computer is called ‘zombie computer’. The result of this threat is the victim’s computer, which is the bot will be used for malicious activities and for a larger scale attack like DDoS.
Rootkit
 A rootkit is a computer program designed to provide continued privileged access to a computer while actively hiding its presence. Once a rootkit has been installed, the controller of the rootkit will be able to remotely execute files and change system configurations on the host machine.
A rootkit is a computer program designed to provide continued privileged access to a computer while actively hiding its presence. Once a rootkit has been installed, the controller of the rootkit will be able to remotely execute files and change system configurations on the host machine.
Keylogger
 Also known as a keystroke logger, keyloggers can track the real-time activity of a user on his computer. It keeps a record of all the keystrokes made by user keyboard. Keylogger is also a very powerful threat to steal people’s login credential such as username and password.
Also known as a keystroke logger, keyloggers can track the real-time activity of a user on his computer. It keeps a record of all the keystrokes made by user keyboard. Keylogger is also a very powerful threat to steal people’s login credential such as username and password.
These are perhaps the most common security threats that you’ll come across. Apart from these, there are others like spyware, wabbits, scareware, bluesnarfing and many more. Fortunately, there are ways to protect yourself against these attacks.
Why is Computer Security Important?
In this digital era, we all want to keep our computers and our personal information secure and hence computer security is important to keep our personal information protected. It is also important to maintain our computer security and its overall health by preventing viruses and malware which would impact on the system performance.
Computer Security Practices
Computer security threats are becoming relentlessly inventive these days. There is much need for one to arm oneself with information and resources to safeguard against these complex and growing computer security threats and stay safe online. Some preventive steps you can take include:
- Secure your computer physically by:
- Installing reliable, reputable security and anti-virus software
- Activating your firewall, because a firewall acts as a security guard between the internet and your local area network
- Stay up-to-date on the latest software and news surrounding your devices and perform software updates as soon as they become available
- Avoid clicking on email attachments unless you know the source
- Change passwords regularly, using a unique combination of numbers, letters and case types
- Use the internet with caution and ignore pop-ups, drive-by downloads while surfing
- Taking the time to research the basic aspects of computer security and educate yourself on evolving cyber-threats
- Perform daily full system scans and create a periodic system backup schedule to ensure your data is retrievable should something happen to your computer.
Apart from these, there are many ways you can protect your computer system. Aspects such as encryption and computer cleaners can assist in protecting your computers and its files.
Unfortunately, the number of cyber threats are increasing at a rapid pace and more sophisticated attacks are emerging. So, having a good foundation in cybersecurity concepts will allow you to protect your computer against ever-evolving cyber threats.
The OSI Security Architecture
Security Architecture
for OSI
• ITU-T Recommendation X.800, Security
Architecture for OSI defines systematic way to
• Defining the requirements for security
•
Characterizing
the approaches to satisfying those requirements
ITU-T – international
Telecommunication Union Telecommunication Standardization Sector
OSI
– Open Systems Interconnections
OSI Security
Architecture
The
following concepts are used:
•Security attack: Any actions that compromises the security of information owned by an
organization (or a person)
•Security mechanism: a mechanism that is designed to detect, prevent, or recover from a
security attack
•Security service: a service that enhances the security of the data processing systems
and the information transfers of an organization. The services make use of one
or more security mechanisms to provide the service
Security attacks
•Passive attack: aims to learn or make use of information from the system but does not affect system resources.
•Active attack: attempts to alter system resources or affect their operation
Active Attacks
How to deal with?
•
Detect and recover from
disruption or delay
• It is more feasible than prevention
Security services
• Security service is a service which ensures adequate security of the
systems or of data transfers
• X.800 Recommendation divides security services into 5 categories:
•
Authentication
•
Access control
•
Data confidentiality
•
Data integrity
•
Nonrepudiation
•
Availability
service
Authentication
The authentication service is concerning with assuring that a
communication is authentic:
• The recipient of the message should be sure that the
message came
from the source that it claims to be
• All communicating parties should be sure that the connection is not
interfered with by unauthorized party.
Example: consider a person, using online banking service. Both the user and
the bank should be assured in identities of each other
Access control
This service
controls
•
who can have access to a resource;
•
under what conditions access
can occur;
•
what those accessing are
allowing to do.
Example: in online banking a user may be allowed to see his balance, but not
allowed to make any transactions for some of his accounts
Data confidentiality
The protection of data from unauthorized disclosure (from passive
attacks).
• Connection confidentiality
•
Connectionless confidentiality
•
Selective field confidentiality
•
Traffic-Flow Confidentiality
Data Integrity
• The assurance that data received are exactly as sent by an
authorized entity, i.e. contain
•
no modification
•
no insertion
•
no deletion
•
no replay
• Protection from active attacks
• It may be
•
integrity with recovery, or
•
Integrity without recovery
(detection only)
Security mechanisms
Security mechanisms are used to implement security
services. They include (X.800):
• Encipherment
• Digital signature
• Access Control mechanisms
• Data Integrity mechanisms
• Authentication Exchange
• Traffic Padding
• Routing Control
• Notarisation
================================================
What is Classical Encryption Techniques
Definitions of Terms *
- Plaintext: original message
- Ciphertext: coded message
- Enciphering or encryption: the process of converting from plaintext to ciphertext
- Deciphering or decryption: the process of restoring the plaintext from the ciphertext
The many schemes used for encryption constitute the area of study known as cryptography. Such a scheme is known as a cryptographic system (cryptosystem) or a cipher. Techniques used for deciphering a message without any knowledge of the enciphering details fall into the area of cryptanalysis. Cryptanalysis is what the layperson calls "breaking the code". The areas of cryptography and cryptanalysis together are called cryptology.
Classical Cryptography:
In the classical cryptography the original data i.e., the plain text is transformed into the encoded format i.e. cipher text so that we can transmit this data through insecure communication channels. A data string which known as key is used to control the transformation of the data from plain text to cipher text. This arrangement helps to keep data safe as it required the key for extracting the original information from the cipher text. Without the key no one can read the data. In this technique it is assumed that the only authorized receiver has the key.
Classical Cryptography has two types of techniques:
Symmetric Cipher Model
A symmetric encryption scheme has five ingredients (as shown in the following figure):
- Plaintext: This is the original intelligible message or data that is fed into the algorithm as input.
- Encryption algorithm: The encryption algorithm performs various substitutions and transformations on the plaintext.
- Secret key: The secret key is also input to the encryption algorithm. The key is a value independent of the plaintext and of the algorithm. The algorithm will produce a different output depending on the specific key being used at the time. The exact substitutions and transformations performed by the algorithm depend on the key.
- Ciphertext: This is the scrambled (unintelligible) message produced as output.
- It depends on the plaintext and the secret key. For a given message, two different keys will produce two different ciphertexts.
- Decryption algorithm: This is essentially the encryption algorithm run in reverse. It takes the ciphertext and the secret key and produces the original plaintext.
Encryption Requirements *
There are two requirements for secure use of conventional encryption:
- The encryption algorithm must be strong.
- At a minimum, an opponent who knows the algorithm and has access to one or more ciphertexts would be unable to decipher the ciphertext or figure out the key.
- In a stronger form, the opponent should be unable to decrypt ciphertexts or discover the key even if he or she has a number of ciphertexts together with the plaintext for each ciphertext.
- Sender and receiver must have obtained copies of the secret key in a secure fashion and must keep the key secure. If someone can discover the key and knows the algorithm, all communication using this key is readable.
Advantages of Classical Cryptography:
- While employing the one-time pad, it is unbreakable.
- It is easy to do manually, no computer required.
- It protects the plain text from casual snooping.
Disadvantages of Classical Cryptography:
- While employing the one-time pad, it is cumbersome and requires a personal meetup to exchange the pads.
- If not employing the OTP, anyone who is even remotely interested in knowing what you wrote and knows about cryptography will be able to break the encryption.
The DES (Data Encryption Standard) algorithm is a symmetric-key block cipher created in the early 1970s by an IBM team and adopted by the National Institute of Standards and Technology (NIST). The algorithm takes the plain text in 64-bit blocks and converts them into ciphertext using 48-bit keys.
Since it’s a symmetric-key algorithm, it employs the same key in both encrypting and decrypting the data. If it were an asymmetrical algorithm, it would use different keys for encryption and decryption.
DES is based on the Feistel block cipher, called LUCIFER, developed in 1971 by IBM cryptography researcher Horst Feistel. DES uses 16 rounds of the Feistel structure, using a different key for each round.
DES became the approved federal encryption standard in November 1976 and subsequently reaffirmed as the standard in 1983, 1988, and 1999. For the longest time, DES was the data encryption standard in information security.
The Data Encryption Standard (DES) is a symmetric-key block cipher published by the National Institute of Standards and Technology (NIST).
DES is an implementation of a Feistel Cipher. It uses 16 round Feistel structure. The block size is 64-bit. Though, key length is 64-bit, DES has an effective key length of 56 bits, since 8 of the 64 bits of the key are not used by the encryption algorithm (function as check bits only). General Structure of DES is depicted in the following illustration
The algorithm process breaks down into the following steps:
- The process begins with the 64-bit plain text block getting handed over to an initial permutation (IP) function.
- The initial permutation (IP) is then performed on the plain text.
- Next, the initial permutation (IP) creates two halves of the permuted block, referred to as Left Plain Text (LPT) and Right Plain Text (RPT).
- Each LPT and RPT goes through 16 rounds of the encryption process.
- Finally, the LPT and RPT are rejoined, and a Final Permutation (FP) is performed on the newly combined block.
- The result of this process produces the desired 64-bit ciphertext.
The encryption process step (step 4, above) is further broken down into five stages:
- Key transformation
- Expansion permutation
- S-Box permutation
- P-Box permutation
- XOR and swap
For decryption, we use the same algorithm, and we reverse the order of the 16 round keys.
Next, to better understand what is DES, let us learn the various modes of operation for DES
Since DES is based on the Feistel Cipher, all that is required to specify DES is −
- Round function
- Key schedule
- Any additional processing − Initial and final permutation
Initial and Final Permutation
The initial and final permutations are straight Permutation boxes (P-boxes) that are inverses of each other. They have no cryptography significance in DES. The initial and final permutations are shown as follows −
Round Function
The heart of this cipher is the DES function, f. The DES function applies a 48-bit key to the rightmost 32 bits to produce a 32-bit output.
DES Analysis
The DES satisfies both the desired properties of block cipher. These two properties make cipher very strong.
Avalanche effect − A small change in plaintext results in the very great change in the ciphertext.
Completeness − Each bit of ciphertext depends on many bits of plaintext.
During the last few years, cryptanalysis have found some weaknesses in DES when key selected are weak keys. These keys shall be avoided.
DES has proved to be a very well designed block cipher. There have been no significant cryptanalytic attacks on DES other than exhaustive key search.
Advantages:
- its a 56 bit key. So there are 2^56 possibilities of keys which would take a decade to find the correct key using brute-force attack
- Encryption and decryption takes the same algorithm. Only that the function need to be reversed and the key should be taken in opposite order. This is very convenient for software and hardware requirements.
Disadvantages:(I would say small weaknesses!)
- Weak keys : the key that is selected on the rounds are a problem . During splitting of keys to two half and swapping them might throw up the same result if they have continuous 1’s and 0’s. Thins ends up in using the same key through out the 16-cycles
- There can be same output from the S-Boxes on different inputs on permutation. These are called Semi weak keys.
- If the message is encrypted with a particular key, and is taken 1’s compliment of that encryption will be same as that of the encryption of the compliment message and compliment key.
A block cipher processes the data blocks of fixed size. Usually, the size of a message is larger than the block size. Hence, the long message is divided into a series of sequential message blocks, and the cipher operates on these blocks one at a time.
Electronic Code Book (ECB) Mode
This mode is a most straightforward way of processing a series of sequentially listed message blocks.
Operation
The user takes the first block of plaintext and encrypts it with the key to produce the first block of ciphertext.
He then takes the second block of plaintext and follows the same process with same key and so on so forth.
The ECB mode is deterministic, that is, if plaintext block P1, P2,…, Pm are encrypted twice under the same key, the output ciphertext blocks will be the same.
In fact, for a given key technically we can create a codebook of ciphertexts for all possible plaintext blocks. Encryption would then entail only looking up for required plaintext and select the corresponding ciphertext. Thus, the operation is analogous to the assignment of code words in a codebook, and hence gets an official name − Electronic Codebook mode of operation (ECB). It is illustrated as follows −
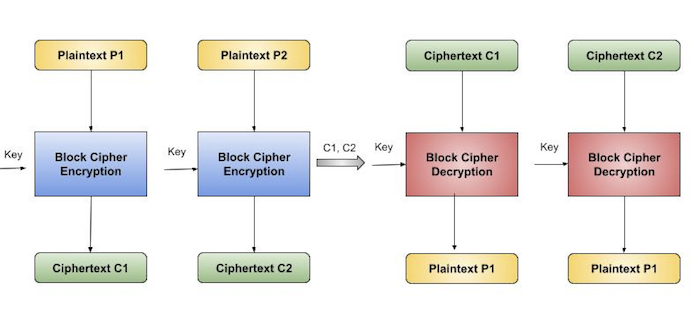
Analysis of ECB Mode
In reality, any application data usually have partial information which can be guessed. For example, the range of salary can be guessed. A ciphertext from ECB can allow an attacker to guess the plaintext by trial-and-error if the plaintext message is within predictable.
For example, if a ciphertext from the ECB mode is known to encrypt a salary figure, then a small number of trials will allow an attacker to recover the figure. In general, we do not wish to use a deterministic cipher, and hence the ECB mode should not be used in most applications.
Cipher Block Chaining (CBC) Mode
CBC mode of operation provides message dependence for generating ciphertext and makes the system non-deterministic.
Operation
The operation of CBC mode is depicted in the following illustration. The steps are as follows −
Load the n-bit Initialization Vector (IV) in the top register.
XOR the n-bit plaintext block with data value in top register.
Encrypt the result of XOR operation with underlying block cipher with key K.
Feed ciphertext block into top register and continue the operation till all plaintext blocks are processed.
For decryption, IV data is XORed with first ciphertext block decrypted. The first ciphertext block is also fed into to register replacing IV for decrypting next ciphertext block.
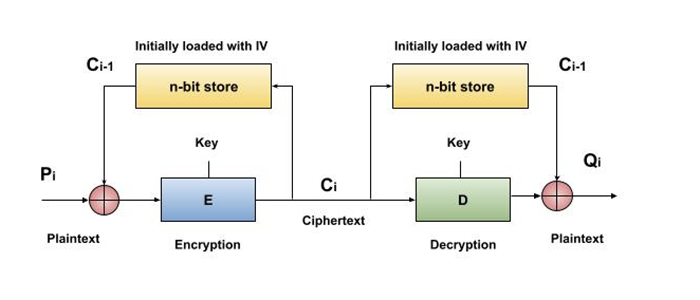
Analysis of CBC Mode
In CBC mode, the current plaintext block is added to the previous ciphertext block, and then the result is encrypted with the key. Decryption is thus the reverse process, which involves decrypting the current ciphertext and then adding the previous ciphertext block to the result.
Advantage of CBC over ECB is that changing IV results in different ciphertext for identical message. On the drawback side, the error in transmission gets propagated to few further block during decryption due to chaining effect.
It is worth mentioning that CBC mode forms the basis for a well-known data origin authentication mechanism. Thus, it has an advantage for those applications that require both symmetric encryption and data origin authentication.
Cipher Feedback (CFB) Mode
In this mode, each ciphertext block gets ‘fed back’ into the encryption process in order to encrypt the next plaintext block.
Operation
The operation of CFB mode is depicted in the following illustration. For example, in the present system, a message block has a size ‘s’ bits where 1 < s < n. The CFB mode requires an initialization vector (IV) as the initial random n-bit input block. The IV need not be secret. Steps of operation are −
Load the IV in the top register.
Encrypt the data value in top register with underlying block cipher with key K.
Take only ‘s’ number of most significant bits (left bits) of output of encryption process and XOR them with ‘s’ bit plaintext message block to generate ciphertext block.
Feed ciphertext block into top register by shifting already present data to the left and continue the operation till all plaintext blocks are processed.
Essentially, the previous ciphertext block is encrypted with the key, and then the result is XORed to the current plaintext block.
Similar steps are followed for decryption. Pre-decided IV is initially loaded at the start of decryption.
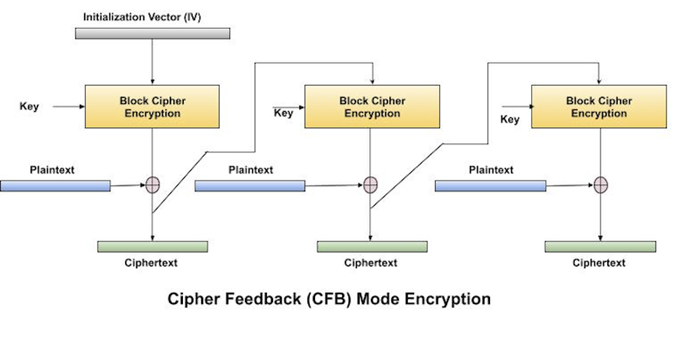
Analysis of CFB Mode
CFB mode differs significantly from ECB mode, the ciphertext corresponding to a given plaintext block depends not just on that plaintext block and the key, but also on the previous ciphertext block. In other words, the ciphertext block is dependent of message.
CFB has a very strange feature. In this mode, user decrypts the ciphertext using only the encryption process of the block cipher. The decryption algorithm of the underlying block cipher is never used.
Apparently, CFB mode is converting a block cipher into a type of stream cipher. The encryption algorithm is used as a key-stream generator to produce key-stream that is placed in the bottom register. This key stream is then XORed with the plaintext as in case of stream cipher.
By converting a block cipher into a stream cipher, CFB mode provides some of the advantageous properties of a stream cipher while retaining the advantageous properties of a block cipher.
On the flip side, the error of transmission gets propagated due to changing of blocks.
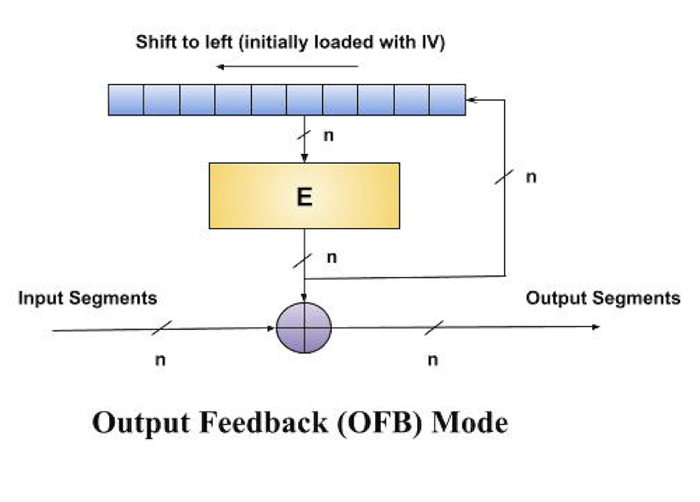
Output Feedback (OFB) Mode
It involves feeding the successive output blocks from the underlying block cipher back to it. These feedback blocks provide string of bits to feed the encryption algorithm which act as the key-stream generator as in case of CFB mode.
The key stream generated is XOR-ed with the plaintext blocks. The OFB mode requires an IV as the initial random n-bit input block. The IV need not be secret.
The operation is depicted in the following illustration −
Counter (CTR) Mode
It can be considered as a counter-based version of CFB mode without the feedback. In this mode, both the sender and receiver need to access to a reliable counter, which computes a new shared value each time a ciphertext block is exchanged. This shared counter is not necessarily a secret value, but challenge is that both sides must keep the counter synchronized.
Operation
Both encryption and decryption in CTR mode are depicted in the following illustration. Steps in operation are −
Load the initial counter value in the top register is the same for both the sender and the receiver. It plays the same role as the IV in CFB (and CBC) mode.
Encrypt the contents of the counter with the key and place the result in the bottom register.
Take the first plaintext block P1 and XOR this to the contents of the bottom register. The result of this is C1. Send C1 to the receiver and update the counter. The counter update replaces the ciphertext feedback in CFB mode.
Continue in this manner until the last plaintext block has been encrypted.
The decryption is the reverse process. The ciphertext block is XORed with the output of encrypted contents of counter value. After decryption of each ciphertext block counter is updated as in case of encryption.
UNIT - 2
Algorithm
The RSA algorithm holds the following features −
RSA algorithm is a popular exponentiation in a finite field over integers including prime numbers.
The integers used by this method are sufficiently large making it difficult to solve.
There are two sets of keys in this algorithm: private key and public key.
You will have to go through the following steps to work on RSA algorithm −
Step 1: Generate the RSA modulus
The initial procedure begins with selection of two prime numbers namely p and q, and then calculating their product N, as shown −
N=p*q
Here, let N be the specified large number.
Step 2: Derived Number (e)
Consider number e as a derived number which should be greater than 1 and less than (p-1) and (q-1). The primary condition will be that there should be no common factor of (p-1) and (q-1) except 1
Step 3: Public key
The specified pair of numbers n and e forms the RSA public key and it is made public.
Step 4: Private Key
Private Key d is calculated from the numbers p, q and e. The mathematical relationship between the numbers is as follows −
ed = 1 mod (p-1) (q-1)
The above formula is the basic formula for Extended Euclidean Algorithm, which takes p and q as the input parameters.
Encryption Formula
Consider a sender who sends the plain text message to someone whose public key is (n,e). To encrypt the plain text message in the given scenario, use the following syntax −
C = Pe mod n
Decryption Formula
The decryption process is very straightforward and includes analytics for calculation in a systematic approach. Considering receiver C has the private key d, the result modulus will be calculated as −
Generating RSA keys
The following steps are involved in generating RSA keys −
Create two large prime numbers namely p and q. The product of these numbers will be called n, where n= p*q
Generate a random number which is relatively prime with (p-1) and (q-1). Let the number be called as e.
Calculate the modular inverse of e. The calculated inverse will be called as d.
Plaintext = Cd mod n
Public Key Cryptography
Unlike symmetric key cryptography, we do not find historical use of public-key cryptography. It is a relatively new concept.
Symmetric cryptography was well suited for organizations such as governments, military, and big financial corporations were involved in the classified communication.
With the spread of more unsecure computer networks in last few decades, a genuine need was felt to use cryptography at larger scale. The symmetric key was found to be non-practical due to challenges it faced for key management. This gave rise to the public key cryptosystems.
The process of encryption and decryption is depicted in the following illustration −
The most important properties of public key encryption scheme are −
Different keys are used for encryption and decryption. This is a property which set this scheme different than symmetric encryption scheme.
Each receiver possesses a unique decryption key, generally referred to as his private key.
Receiver needs to publish an encryption key, referred to as his public key.
Some assurance of the authenticity of a public key is needed in this scheme to avoid spoofing by adversary as the receiver. Generally, this type of cryptosystem involves trusted third party which certifies that a particular public key belongs to a specific person or entity only.
Encryption algorithm is complex enough to prohibit attacker from deducing the plaintext from the ciphertext and the encryption (public) key.
Though private and public keys are related mathematically, it is not be feasible to calculate the private key from the public key. In fact, intelligent part of any public-key cryptosystem is in designing a relationship between two keys.
There are three types of Public Key Encryption schemes. We discuss them in following sections
========================================================








